Key Takeaways:
- Automated Extraction: Convert PDFs, emails, and scanned files into structured JSON or CSV.
- Parseur Advantage: Offers an API and a web app for seamless integration and operational management.
- Compliance-Ready: Built-in GDPR, cross-border, and security features support legal adherence.
- Operational Efficiency: Enables teams to monitor, adjust, and refine parsing without additional development.
A data extraction API for documents enables businesses to convert PDFs, scanned files, and emails into structured data formats like JSON or CSV, powering automation, analytics, and compliance-ready workflows. Most enterprise data is unstructured: The Intelligent Document Processing (IDP) market suggests 80–90% of new business data is unstructured (documents, images, etc.), but only about 18% of organizations actively use it. Unlike web scraping APIs, which often raise intellectual property and anti-scraping legal risks, document parsing APIs operate within strict privacy, data protection, and contractual frameworks.
This guide covers the legal considerations for data extraction APIs you need to know in 2026, including GDPR compliance, data processing agreements (DPAs), cross-border data transfer rules (EU, U.S., Brazil, India), and security requirements for handling sensitive data.
What Changes Legally When You Parse Documents (Not Websites)?
Parsing documents through a data extraction API fundamentally differs from web scraping, and the legal landscape changes. When you parse PDFs, emails, or scanned files, you are not harvesting data from public sources, but processing files you already lawfully hold or have received. This moves the primary legal focus from “permission to access” to privacy, compliance, and contractual responsibilities.
Define Roles Early: Controller vs. Processor
Under GDPR (Article 28) and similar privacy laws worldwide, it’s essential to determine whether you are acting as a data controller or a data processor:
- Controllers decide why and how personal data is processed. They are primarily responsible for legal compliance, including determining lawful bases, handling data subject rights, and defining retention policies. However, the weight of these obligations doesn’t look the same for every organization. Smaller businesses often manage relatively limited datasets, while larger enterprises face significantly greater volumes and complexity.
This contrast is reflected in industry surveys highlighting how compliance responsibilities scale with organizational size. According to the Information Commissioner’s Office, in 2025, a representative survey found 83% of organizations acting as data controllers processed personal data for fewer than 1,000 individuals annually, while 54% of large organizations processed data for over 10,000 data subjects.
- Processors act solely on the controller’s documented instructions. They apply appropriate technical and organizational measures, maintain processing records, and assist the controller with compliance requirements.
In document parsing workflows, your organization is typically the controller, while your chosen API provider, such as Parseur, acts as the processor. This distinction drives everything from Data Processing Agreements (DPAs) to security obligations and breach notification timelines.
Core Privacy Principles To Build Around (EU GDPR)
When you move from document parsing to document data extraction APIs, you’re no longer dealing with casual “data scraping”; you’re processing information you already lawfully hold or receive. That changes your legal obligations squarely into privacy and compliance territory, with the EU GDPR setting the global benchmark. This shift highlights an important distinction: using a document extraction API isn’t just about technical efficiency; it’s about compliance. Extracted data often includes personal or sensitive information, meaning organizations must treat it under strict GDPR data processing obligations.
Balancing automation with privacy requirements ensures that businesses can take advantage of the power of document extraction APIs while staying compliant with data minimization, purpose limitation, and other core principles.
1. GDPR principles as your API’s foundation (Article 5)
Every workflow that ingests PDFs, emails, or forms must reflect GDPR’s core principles:
- Lawfulness, fairness, and transparency: Ensure every data flow has a valid legal basis (e.g., contract execution, consent) and clear user communication.
- Purpose limitation: Collect data strictly for defined purposes; no “extra” processing beyond your contract.
- Data minimisation: Extract only what’s essential (e.g., invoice totals, not entire attachments).
- Accuracy: Verify extracted fields to prevent errors from cascading into downstream systems.
- Storage limitation: Use TTLs or auto-deletion to avoid holding data longer than necessary.
- Integrity & confidentiality: Encrypt everything, lock down access, and monitor for anomalies.
Best practice: Anchor these principles directly into your API defaults, for example, enabling field-level extraction to minimise data, or setting TTLs (time-to-live) for document storage.
2. Data protection by design and default (Article 25)
GDPR requires privacy to be integrated by design and by default. For a document extraction API, this means:
- Technical measures: Encryption at rest and in transit, pseudonymisation of extracted data, and strong authentication.
- Organisational measures: Access controls, employee training, and regular security audits.
Mapping these safeguards to product features ensures compliance and builds customer trust.
3. Records of processing activities (Article 30)
Controllers and processors must maintain a Record of Processing Activities (RoPA). For APIs, this means documenting:
- What data types are processed (e.g., invoices, contracts, forms)?
- Why do you process them and under what legal basis?
- Where data flows, how long you keep it, and what protections apply?
Offering customers RoPA-ready templates can simplify their compliance and deepen trust.
4. Breach notifications (Article 33)
Under GDPR, you have 72 hours to notify regulators after becoming aware of a breach. To comply:
- A clear incident response playbook with roles, timelines, and regulator contact details.
- Regular drills to prove you can execute under pressure.
Key takeaway: GDPR compliance isn’t just a checkbox; it’s a framework to embed privacy, security, and accountability into every stage of document data extraction.
How does Parseur put GDPR into practice?
At Parseur, data protection isn’t an afterthought; it’s woven into every aspect of its document parsing workflow. From infrastructure to access controls, Parseur prioritizes security, compliance, and your control over data. For full details, visit Parseur’s official Privacy & GDPR, Security & Privacy, and Legal pages.
- Encryption everywhere: Data is encrypted in transit and at rest.
- Access control & monitoring: Role-based permissions, mandatory authentication, and real-time system monitoring.
- Data minimization & retention: Only essential fields are extracted; documents can be auto-deleted post-processing.
- Independent validation: In 2025, Parseur earned an A+ grade from Astra Security after passing an in-depth penetration test and remediating all identified vulnerabilities.
These safeguards make it easier for customers to meet compliance obligations while ensuring the API remains secure, trustworthy, and audit-ready.
Contract Stack: Make The Relationships Defensible
Solid contracts are the backbone of compliant document extraction APIs. They establish roles, allocate risk, and prove to regulators and customers that you take privacy and security seriously.
1. Data Processing Agreement (DPA) – Article 28 GDPR
A DPA is mandatory when you act as a processor for an EU controller. It must:
- Define the scope, nature, and purpose of processing.
- Set instructions from the controller as binding.
- Require confidentiality, security measures, and breach notifications.
- Allow audits and inspections by the controller or a third-party auditor.
- Bind subprocessors through equivalent obligations.
Sample DPA Clause Highlights:
- “Processor shall maintain technical and organisational measures to ensure a level of security appropriate to the risk, including encryption of personal data in transit and at rest.”
- “Processor shall notify Controller without undue delay and, where feasible, no later than 24 hours after becoming aware of a Personal Data Breach.”
- “Processor shall assist Controller in responding to Data Subject Requests, including access, erasure, and portability requests.”
2. Subprocessor transparency
Your customers will expect to know who touches their data.
- Publish a subprocessor list (names, locations, services provided).
- Create a change-notice process, email notifications, or a public changelog with a grace period for objections.
This builds trust and meets GDPR’s “flow-down” obligations.
3. Security exhibits
Regulators want to see your security commitments in writing. Attach a Security Exhibit to your DPA, including:
- Minimum controls: Encryption in transit (TLS 1.2+) and at rest (AES-256), strong authentication, and vulnerability management.
- Breach handling: Notification timelines aligned with Article 33 (72 hours to regulators) and customer SLAs.
- Audit rights: Annual third-party penetration testing (like Parseur’s A+ audit by Astra Security) and remediation requirements.
4. Data ownership & Intellectual Property (IP)
Clarify who owns what:
- Inputs (documents): Remain with the customer.
- Outputs (extracted JSON): Typically customer-owned, but specified in the contract.
- Vendor IP: Processing methods, models, and platform code stay with you.
Legal Caveat:
- In the U.S., extracted facts aren’t copyrightable (Feist Publications v. Rural), but the original document may still be protected.
- In the EU, database rights (Directive 96/9/EC) may restrict bulk extraction/re-use of substantial parts of a protected database; consult counsel when dealing with large datasets.
Cross-Border Data Transfers (EU → Non-EU)
Processing EU personal data outside the European Economic Area (EEA) triggers GDPR Chapter V obligations. Articles 44–49 require you to adopt a valid transfer mechanism to ensure equivalent data protection standards.
1. General Rule: No transfer without adequate safeguards
A “transfer” occurs when EU personal data is accessed from, transmitted to, or stored in a non-EEA country. Controllers and processors must ensure lawful mechanisms are in place before transferring.
2. Lawful transfer mechanisms
Adequacy Decisions (Art. 45):
The European Commission can declare a country’s laws “adequate.”
- Example: The EU-U.S. Data Privacy Framework (DPF), adopted July 10, 2023, allows compliant U.S. companies to receive EU personal data without additional safeguards.
- Official EU Commission DPF Page.
Standard Contractual Clauses (SCCs) (Art. 46):
Pre-approved contractual terms binding the data importer to EU-level protections.
- Must be supplemented by a Transfer Impact Assessment (TIA) to assess local laws and practices (per EDPB Recommendations 01/2020).
- Include technical measures like encryption and data masking to mitigate surveillance risks.
Binding Corporate Rules (BCRs) (Art. 47):
Internal codes of conduct for multinational groups, approved by EU regulators.
Derogations (Art. 49):
Narrow exceptions like explicit consent or necessity for contract performance; use sparingly.
3. Transfer Impact Assessment (TIA) – EDPB best practice
When relying on SCCs, conduct and document a TIA:
- Map data flows and destination jurisdictions.
- Assess the recipient country’s surveillance laws and potential access risks.
- Apply additional safeguards where needed (e.g., end-to-end encryption, split-key storage).
- Record decisions and update periodically.
4. Parseur’s cross-border approach
- EU Data Residency: Parseur offers EU-based data centers to minimize cross-border transfers.
- SCCs & DPF: Where transfers are unavoidable, Parseur relies on 2021 SCCs combined with TIAs and participates in the EU-U.S. DPF via certified subprocessors.
- Encryption: All data is encrypted in transit (TLS 1.2+) and at rest (AES-256), ensuring data remains protected regardless of geography.
- Transparency: Customers can review Parseur’s data flow diagrams and subprocessor list anytime.
Read our Data Processing Agreement
Transfer Decision Tree (GDPR):
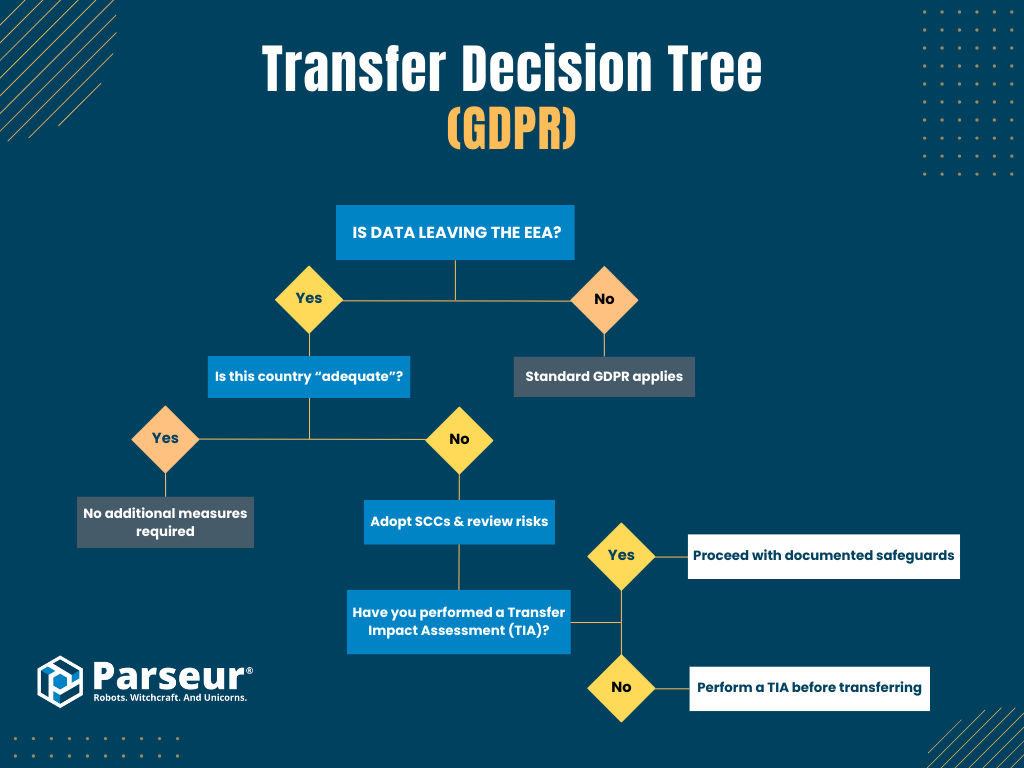
- Is data leaving the EEA?
- No: Standard GDPR applies.
- Yes: Continue below.
- Is the destination country deemed “adequate” by the EU?
- Yes: No additional measures required.
- No: Adopt Standard Contractual Clauses (SCCs) and review transfer risks.
- Have you assessed risk via a Transfer Impact Assessment (TIA)?
- Yes: Proceed with documented safeguards.
- No: Perform a TIA before transferring.
SCCs + TIAs checklist (practical compliance)
- Execute SCCs using the latest 2021 modular templates.
- Conduct a Transfer Impact Assessment (TIA):
- Assess local laws of destination (e.g., surveillance risks).
- Document supplementary measures (e.g., encryption, access restrictions).
- Use technical safeguards: End-to-end encryption, strict access controls.
- Maintain evidence: Prepare signed SCCs, TIAs, and audit logs for regulators.
- Reassess periodically: At least annually or if destination laws change.
By following these steps, businesses can ensure that document extraction APIs like Parseur align with data protection obligations, especially when processing customer or operational data globally.
Other Key Jurisdictions To Watch
While GDPR remains the global benchmark, other major jurisdictions are rapidly advancing their own privacy and data protection regimes. If your document extraction API processes data from these regions, you must adapt your compliance posture accordingly.
Swiss FADP (revFADP, in force since 1 Sept 2023)
Cross-border transfers are allowed only under conditions; safeguards depend on the destination country’s adequacy and must follow FDPIC guidance. Breach notification to the FDPIC is required where a security incident is likely to result in a high risk to the personality or fundamental rights of data subjects; guidance clarifies timing and content.
If you’re established outside Switzerland but process personal data in Switzerland, you may need to appoint a Swiss representative (Art. 14 FADP).
What this means for an extraction API provider/consumer:
- Run as a processor on documented instructions, sign a DPA, and publish a sub-processor list with change notices.
- Offer transfer mechanisms compatible with Switzerland (e.g., SCCs with Swiss addenda) and regional processing options where feasible.
- Maintain a breach playbook aligned to the FDPIC’s “likely high risk” standard.
California CCPA (as amended by CPRA)
CCPA/CPRA grants consumer rights (e.g., correct, limit use of sensitive PI) and is enforced by the CA Attorney General and the California Privacy Protection Agency. Service-provider contracts must restrict use/retention/disclosure, prohibit sale/share, require assistance with consumer requests, and include flow-downs, codified in CPPA regulations §7051.
What this means for an extraction API provider/consumer:
- Contract the vendor as a service provider with §7051-compliant terms; configure logs/exports to help handle access/correction/deletion requests.
- Implement reasonable security (encryption, access controls) and retention limits so extracted JSON isn’t kept longer than necessary.
Singapore PDPA
- Comply with core Data Protection Obligations (Accountability, Consent, Purpose Limitation, Notification, Accuracy, Protection, Retention Limitation, Transfer Limitation, etc.).
- Mandatory data-breach notification to PDPC and affected individuals when thresholds are met; PDPC’s guide sets out timelines and the C.A.R.E. steps.
What this means for an extraction API provider/consumer:
- Expose retention/deletion controls, document purpose limitation, and apply transfer safeguards for overseas processing.
- Maintain an incident-response plan consistent with PDPC’s breach-management guidance.
Brazil – Lei Geral de Proteção de Dados (LGPD)
Brazil’s LGPD (Law No. 13,709/2018) mirrors many GDPR principles and has been fully enforceable since August 2021.
- Scope & Principles: Applies to any entity processing personal data in Brazil or offering services to individuals there. Principles include lawfulness, purpose limitation, adequacy, necessity, transparency, and security.
- Legal Bases: These are similar to the GDPR’s lawful bases (e.g., consent, contractual necessity, legitimate interests).
- Regulator: The Autoridade Nacional de Proteção de Dados (ANPD) is actively issuing guidelines and imposing sanctions.
- Cross-Border Transfers: Permitted only with adequacy decisions, contractual clauses, or specific consent.
- Parseur Alignment: Parseur’s granular access controls, encryption, and clear subprocessors list align with LGPD’s security and accountability requirements, making it easier for customers to meet compliance obligations.
India – Digital Personal Data Protection (DPDP) Act, 2023
India’s DPDP Act, 2023, introduces a complete framework for handling personal data and is set to reshape global data strategies.
- Status: Enacted in August 2023; operational rules and enforcement framework are still pending as of 2025.
- Key Features:
- Lawful Processing: Requires consent or specific legitimate uses defined by law.
- Data Fiduciary Obligations: Similar to controllers under GDPR, must ensure security, purpose limitation, and breach notification.
- Significant Data Fiduciaries: Entities meeting size/impact thresholds must appoint a Data Protection Officer (DPO) and conduct regular audits.
- Cross-Border Transfers: Restricted; detailed rules expected in 2025.
- Parseur Alignment: With data minimisation features (extracting only required fields) and audit logs, Parseur provides strong technical support for organizations preparing for DPDP compliance.
Security, Retention, And Deletion: Make It Provable
Legal frameworks demand strong security and retention practices and evidence that they exist and operate effectively. For document extraction APIs, this means building privacy-by-design controls and being ready to demonstrate compliance to regulators or customers.
Principles → controls mapping
Data Minimisation (GDPR Art. 5, LGPD Art. 6, DPDP Sec. 7):
Extract only the fields you need. Parseur supports field-level extraction, ensuring personal data that is not required never enters your systems.
Storage Limitation (GDPR Art. 5(1)(e)):
Define Time-to-Live (TTL) for stored documents and extracted data. Parseur allows automatic deletion after a configurable retention period.
Integrity & Confidentiality (GDPR Art. 5(1)(f), LGPD Art. 6(VII), DPDP Sec. 8):
Use encryption in transit (TLS 1.2+) and at rest (AES-256), and enforce role-based access controls (RBAC). Parseur logs all access events immutably for full traceability.
Retention schedules & deletion protocols
- Create a retention schedule by document type (e.g., invoices: 7 years, CVs: 6 months).
- Enforce auto-purge rules to prevent unnecessary accumulation of personal data.
- Maintain immutable audit logs to prove compliance during audits or investigations. Parseur provides immutable logs of document processing, webhook deliveries, and user actions.
Incident response & breach management
- GDPR Breach Notifications (Art. 33): Notify supervisory authorities within 72 hours.
- U.S. State Breach Laws: Many require prompt notification to affected individuals.
- Best Practice: Maintain a breach runbook with a RACI matrix (Responsible, Accountable, Consulted, Informed) to clarify roles during incidents.
- Parseur’s Security Readiness: Backed by an A+ security audit and pentest certification (Astra, Aug 2025), demonstrating continuous testing and remediation of vulnerabilities.
DPIA & Risk Assessment For Document Extraction
A Data Protection Impact Assessment (DPIA) is a structured process for identifying and mitigating risks to personal data before starting high-risk processing. Under GDPR Art. 35, a DPIA is mandatory when processing:
- Large-scale sensitive data (health, biometrics, financials).
- Systematic monitoring or profiling.
- New technologies with potential high risk to rights and freedoms.
For document extraction APIs, DPIAs often trigger because PDFs, scans, or email attachments may contain hidden PII/PHI, and machine learning-based extraction can misclassify sensitive data.
Typical risks to assess
- Over-collection: Extracting fields beyond business necessity.
- Hidden PII/PHI: Sensitive data embedded in attachments without clear labeling.
- Cross-border transfers: Exposing data to jurisdictions without adequate protection.
- Model misclassification: Incorrectly tagging or exposing confidential data.
- Access control gaps: Weak authentication allows unauthorized access to documents.
Parseur’s approach to risk management
Parseur integrates DPIA support by:
- Minimizing over-collection: Users control precisely which fields are extracted.
- Providing access controls & audit logs: Full traceability for compliance checks.
- Offering secure hosting & cross-border safeguards: EU and U.S. data centers, SCCs available upon request.
- Certified Security: A+ rating from Astra’s 2025 Pentest ensures third-party validation of security measures.
“You Own The Outputs?” Copyright & Database Rights Quick Primer
Extracting data from documents raises an important legal question: who owns the resulting structured output (e.g., JSON)?
United States: facts vs. expression
Under U.S. law, facts are not copyrightable. This means the data you extract (like invoice amounts or dates) isn’t protected by copyright. However, the original document may still be protected as a copyrighted work.
- Key takeaway: Ensure your contracts clearly grant rights to process documents and use extracted outputs. Without such clauses, ownership may be disputed.
- Best practice: Define “Input Data” (customer documents) and “Output Data” (extracted structured data) separately in your Data Processing Agreement (DPA) or Terms of Service, assigning ownership explicitly.
European Union: database rights & sui generis protection
In the EU, Database Directive 96/9/EC creates a sui generis right over databases where substantial investment has been made in obtaining, verifying, or presenting the contents.
- Impact: If you bulk-process data from a protected database (e.g., a curated collection of contracts), you may need a license even if the individual facts aren’t protected.
- Key takeaway: Always perform an IP review before mass-extracting structured datasets, and include warranties in contracts that the customer has the right to provide the data.
Practical Steps
- Clarify rights in contracts: Specify ownership and usage rights for inputs and outputs.
- Avoid assumptions: Always confirm that source data can legally be processed.
- Consult counsel: Especially if dealing with EU databases or sensitive proprietary collections.
Practical Compliance Checklist (Copy-Ready)
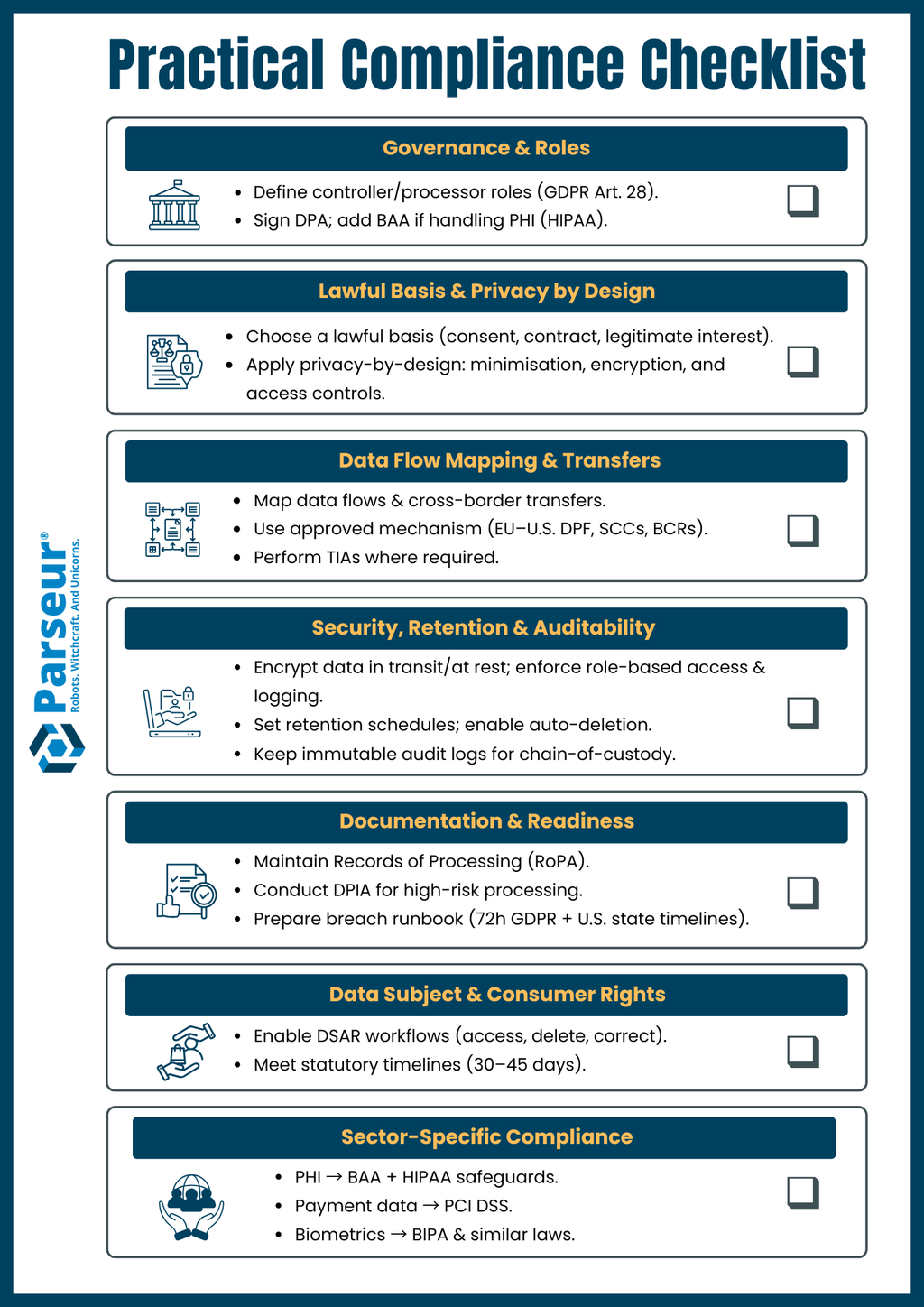
Use this checklist to ensure your document data extraction API is legally defensible and compliant across key jurisdictions:
1. Governance & Roles
- Identify controller/processor roles for each workflow (GDPR Art. 28).
- Execute a Data Processing Agreement (DPA) and Business Associate Agreement (BAA) if processing PHI (HIPAA).
2. Lawful Basis & Privacy by Design
- Select a lawful basis (consent, contract, legitimate interest, etc.) and document purpose limitation & minimisation (GDPR Arts. 5–6).
- Use privacy-by-design defaults: minimal fields, encryption, access controls (GDPR Art. 25).
3. Data Flow Mapping & Transfers
- Map data flows to identify cross-border transfers.
- Use an approved mechanism (EU-U.S. Data Privacy Framework, SCCs, BCRs).
- Perform Transfer Impact Assessments (TIAs) where required (EDPB guidance).
4. Security, Retention & Auditability
- Apply encryption in transit/at rest, role-based access, and logging.
- Set retention schedules per document type and enforce automatic deletion.
- Maintain immutable audit logs for chain-of-custody.
5. Documentation & Readiness
- Maintain Records of Processing Activities (RoPA) (GDPR Art. 30).
- Conduct a Data Protection Impact Assessment (DPIA) for high-risk processing.
- Prepare a breach notification playbook (72-hour GDPR clock + U.S. state timelines).
6. Data Subject & Consumer Rights
- Enforce DSR/DSAR workflows for access, deletion, and correction (GDPR, CCPA/CPRA).
- Respond within statutory timelines (e.g., 30–45 days).
7. Sector-Specific Compliance
- PHI: add BAA (HIPAA) and security rule safeguards.
- Payment Data: ensure PCI DSS compliance.
- Biometric Data: comply with Illinois BIPA and other biometric laws.
How Parseur Handles Data: Security & Privacy Built-In
At Parseur, data protection isn’t an afterthought; it’s a core feature integrated into every step of our document parsing workflows. From secure storage to strict privacy controls, Parseur ensures your business data remains safe, compliant, and accessible only under your control.
For a detailed overview, you can review the official resources on the Parseur Security and Privacy page and the Legal section located at the bottom part of the Parseur website.
Data Storage & Location
All Parseur data is securely hosted within the EU (Netherlands), ensuring physical and legal alignment with GDPR requirements.
Infrastructure & Continuous Security Testing
Parseur maintains vigilant security through continuous monitoring and regular updates. Vulnerability scans cover APIs, dependencies, and infrastructure using OWASP Top 10 and SANS 25 industry standards. Enterprise users can access complete cybersecurity audit reports and penetration test results.
Encryption Protocols
In transit: TLS v1.2 or higher, with legacy protocols (e.g., SSLv2/v3, TLS1.0/1.1) disabled.
At rest: AES-256 encryption.
Data is transmitted over HTTPS secured by Let's Encrypt certificates.
Account Security
Passwords are never stored in plaintext. Parseur uses salted, hashed passwords via the recommended PBKDF2 with SHA-256, employing strong salting and iteration to exceed standard security norms.
Service Uptime & Reliability
Target uptime is 99.9%, with options for enterprise-grade 99.99% uptime. For email ingestion, retries are handled automatically for up to 24 hours, plus optional dual-sending for redundancy.
Privacy & Access Controls
You retain full control over your data. Parseur is strictly a processor operating on your instructions, never selling or sharing your data. Internal access is limited and occurs only for support purposes with your permission. All team members undergo GDPR and data protection training.
Compliance Certifications & Hosting
Parseur uses Google Cloud Platform (GCP) for infrastructure and inherits compliance with ISO 27001. Detailed technical and operational security measures are available in Parseur’s DPA.
Data Retention & Deletion
You control data retention: Set mailbox-specific retention policies (as low as one day) or use the Process-then-Delete feature to remove documents automatically after processing.
Breach Notification Policy
Parseur adheres to transparent incident handling wherein customers are notified of confidentiality breaches within 48 hours of discovery. Security monitoring ensures all access permissions and data are properly encrypted.
Security Questionnaires & Researcher Policy
Enterprise clients can request detailed security responses; otherwise, Parseur provides a prepared list of common security answers. A formal policy exists for security researchers to report potential vulnerabilities safely.
Why Parseur Leads The Way In Document Extraction APIs
Document extraction APIs transform how businesses process data, enabling faster, more accurate, and higher-volume workflows. While many options exist, Parseur stands out by combining a powerful API with an intuitive web app. This combination gives developers seamless integration capabilities while empowering operations teams to manage, monitor, and refine extraction without coding. This dual approach eliminates the need for custom-built monitoring tools, saving time and resources.
In 2026 and beyond, choosing the right document extraction API isn’t just about parsing PDFs; it’s about aligning with your operational needs, security requirements, and compliance obligations. With features like JSON schema definition in a few clicks, automated extraction from emails and attachments, and built-in compliance-friendly workflows, Parseur delivers a practical, automation-ready approach for modern businesses.
If you’re looking to integrate document data extraction into your applications while giving your team easy control over the process, Parseur is the platform built for both sides of the equation, fast to launch, easy to manage, and future-proof.
Frequently Asked Questions
If you’re considering a document extraction API like Parseur, you likely have questions about legality, ownership, and functionality. This FAQ section addresses the most common concerns, helping you understand compliance requirements, practical use cases, and how Parseur simplifies document parsing for developers and operations teams.
-
Is it legal to extract data from customer-submitted PDFs?
-
Usually, yes, if you have an appropriate lawful basis, consent, or contract, along with privacy controls.
-
Do I need consent for every document?
-
It depends on your legal basis and jurisdiction; sensitive data categories may have stricter rules.
-
Do outputs belong to us?
-
Ownership should be defined in your contract; note that under U.S. law (Feist), facts aren’t copyrightable, and EU database rights may apply.
-
What is a document extraction API?
-
A tool that converts unstructured documents like PDFs, emails, and scans into structured data formats such as JSON or CSV.
-
How does Parseur differ from other extraction tools?
-
Parseur offers a developer-friendly API and a web app that allow operations teams to monitor, adjust, and improve parsing without coding.
-
Can I extract tables and key-value pairs from documents?
-
Parseur accurately extracts structured fields, tables, and labeled data from invoices, forms, emails, etc.
-
Do I need a developer to manage Parseur’s workflows?
-
Operations teams can use the web app to define schemas, review documents, and adjust parsing without coding.
Last updated on